Memo Published April 15, 2020 · 3 minute read
How Many Ransomware Attacks Have Happened in Your District?
Anisha Hindocha & Ishan Mehta
Takeaways
- From November 6, 2013 to March 5, 2020, there have been reports of 327 ransomware attacks on public sector entities in the United States, hitting 207 congressional districts. Data tells us that ransomware—when a victims’ systems or data are held hostage until a ransom is paid—on both public and private sector entities is increasing.
- There is a lack of consequences imposed on the perpetrators of these attacks in the United States. From June 2014 to December 2019, law enforcement has issued 6 public indictments against perpetrators of ransomware attacks, and only one arrest has been made. This is part of a larger trend. Third Way has found that, on average, only 3 in 1,000 reported cyber incidents, including ransomware, see an arrest.
- Congress has the opportunity to do something about this during the appropriations process. Members of Congress can raise this issue with relevant agency heads and secretaries during the budget hearings and provide more resources to federal agencies to reduce these attacks and bring perpetrators to justice.
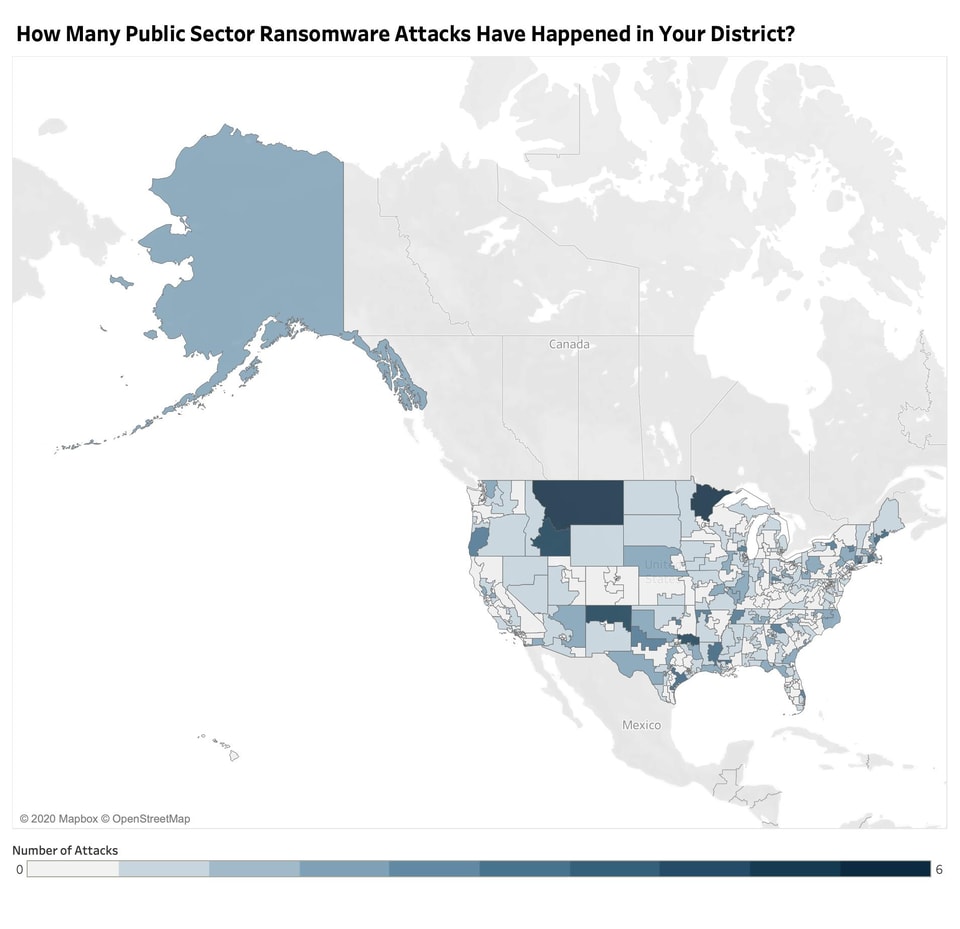
The number of ransomware attacks on the public sector has been steadily increasing since the first reported attack on the Swansea Police Department in Massachusetts in November 2013.1 Ransomware is a form of malicious software (malware) designed to deny access to a computer system or data until a ransom is paid, usually through encrypting the victim’s data.2 Based on publicly available data gathered by StateScoop, Third Way determined 207 House districts or nearly half of all districts have experienced at least one ransomware attack on a state or local public entity.3 As of March 5, 2020, there have been 327 reported ransomware attacks since November 2013. Collectively, 44 public entities have paid over $2.6 million in ransom to regain access to their data. Those victims that have not paid ransom have faced tremendous costs in recovery. Texas is the hardest hit state with 30 reported attacks. Particularly worrisome, ransomware poses a particular concern to the public sector during crises such as the current COVID-19 pandemic.4 For example, the Champaign Urbana Public Health District in Illionois was hit by a strain of ransomware in March, forcing the district to set up an alternate website to provide basic COVID-19 information to the public.5
Congress has done little to help law enforcement impose consequences on the human attackers behind these malicious cyber activities. While these ransomware attacks have become more prevalent, law enforcement has not been able to meet the threat. The Department of Justice has issued indictments publicly against perpetrators of 6 strains of ransomware coming from nations like North Korea, Iran, and Russia, but have made only one arrest.6 More broadly, Third Way has estimated that US law enforcement makes an arrest in less than 1 percent of the total reported malicious cyber incidents occurring per year in the United States.7
Congress has an opportunity to do something about the growing threat of ransomware during the appropriations process. Members should take the opportunity to raise this issue with the heads of relevant federal departments and agencies like the Department of Justice, Federal Bureau of Investigation, Department of State, and the Department of Homeland Security. Third Way created the following map to help members of Congress and their staffs find out how many ransomware attacks have happened to a public entity in their districts, if there has been an indictment in each instance, and if an arrest has been made. You can view the spreadsheet on which this data is based on here.
We would like to thank the team at StateScoop, in particular their Technology Editor Benjamin Freed, for collecting the data used in this research for their Ransomware Map.8